Members
Security
The secure operation of the Internet and the safety of Internet users are getting more and more vital as the Internet is widely deployed as a part of our social infrastructure. The abuse of the Internet existed from the beginning of the Internet history, however, the techniques of attacks are getting cleverer and the impact becomes bigger as more and more important information is exchanged over the Internet. The major kinds of the attacks related to the network services performed over the Internet are roughly categorized into two classes. One is a denial of service or degradation of service quality attack. The other is stealing important information from individual persons or companies. As a preparation phase for these attacks, attackers try to break into computers as a first step. A lot of different kinds of intrusion methods exist and many of them use software vulnerability of the operating system or applications of the target computer. Once a computer is hijacked, attackers use the computer to break into another computer, or use it as a base node to do real attack actions.
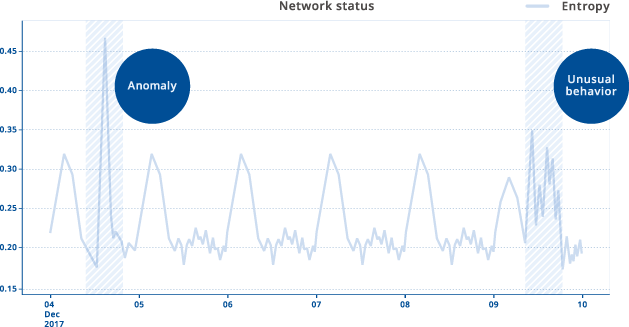
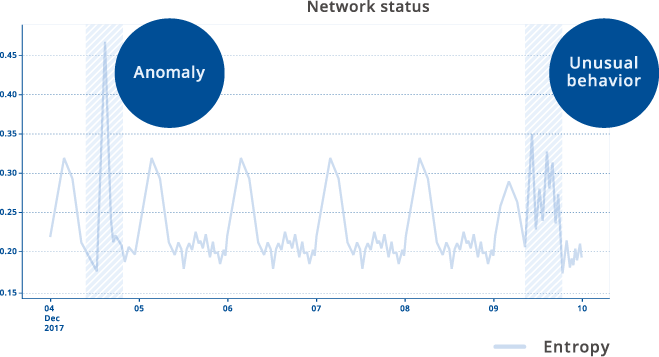
The behavior analysis of communication status is one of the methods to catch unknown or suspicious activities. There are a lot of different services on the Internet and it looks there is no explicit discipline in the datagram, however, we can guess the network status by using specific indexes and perform statistical processes on the data. Such indexes sometimes change when there is a big behavior change. Although these changes do not always mean attacks, we can start more detailed analysis based on the information. Such investigation will make it possible to defend unknown attacks.
A computer virus is one of the oldest threats. The Internet makes it easy for us to share information with other people, but this also contributes attackers to share information of attacking technology. Once a new type of virus is developed, the information is quickly shared and many variants those are slightly different from the original virus are developed. Since these various have different binary codes, it is difficult to find them just to compare the code to the codes found before. One of the approaches to tackle this issue is a binary analysis technology. This analyze the meaning of the code and understand the behavior of the program. By comparing the behavior of the new suspicious program to the behaviors of viruses observed before, we can find a new variant of the known virus.

Protecting computers connected to the Internet is considered almost indispensable recently. We can use various kinds of security products as the leaf protection technology to enhance secure Internet operation. However, a new style of attach methodology appears almost every day. It is not enough just to protect known attacks to make the Internet secure. We are making efforts to research and develop technologies that can capture any suspicious behavior on the network to realize more secure and safer Internet.

